Comments
- No comments found

The recent global outage caused by cybersecurity firm CrowdStrike has far-reaching implications for the cybersecurity industry.
The world experienced a digital pandemic of systems going offline and displaying the dreaded Windows Blue Screen of Death (BSOD), due to a catastrophic failure caused by a flawed file in an update to CrowdStrike cybersecurity customers. The impacts have been obscenely widespread, with many banks, airlines, train stations, financial exchanges, news agencies, supermarkets, and health care providers to name a few.
CrowdStrike is used by almost 60% of Fortune 500 companies and over half of the Fortune 1,000. It is popular in the financial sector, with deployments in eight of the top 10 financial services firms. Many of the biggest technology, healthcare, and manufacturing companies are also customers.
So far, the faulty CrowdStrike update is not attributed to malicious activities, but the impacts have been massive, prompting social media to unofficially designate today as BSOD day!
This outage of CrowdStrike customers on Windows 10 systems reinforces three important aspects.
First, cybersecurity solutions need deep and privileged access to systems, making them more impactful if they are hijacked or malfunction. This access is necessary to make preventative defensive changes before attacks occur, to monitor for stealthy attacks, and to coordinate system-level remediation actions when necessary. But when things go wrong, those permissions then can cause equally impactful damages.
The computing stack is like a layered cake, with data at the top, followed by applications, virtual machines, operating systems, VM managers, firmware, and finally hardware at the bottom. The deeper you go the more potential for problems to be impactful and difficult to remedy. Cyber attackers try to get as far down the stack as possible because they can avoid detection from any layer above and are more difficult to evict. When errors occur, the same relevance applies.
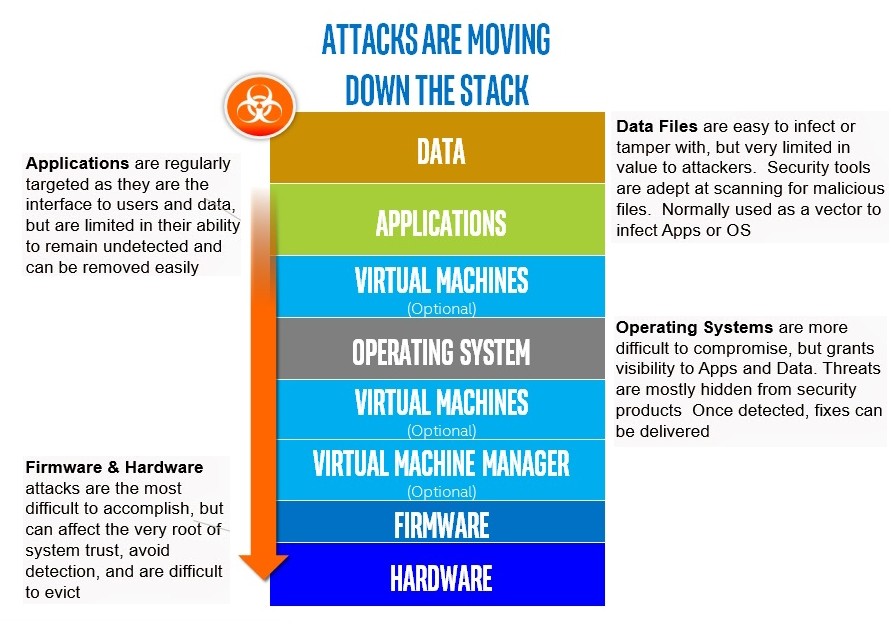
Second, the risk of supply chain attacks is real, and depending on the vendor, they could be catastrophic. CrowdStrike is one of the biggest cybersecurity players in the industry. An accidental or malicious problem in their flagship product, as we have seen, can deliver widespread impacts to the most important sectors. Let’s be glad that this was simply a technical glitch. A malicious package inserted into an update could completely take over systems or permanently destroy them.
Third, bad updates, code bugs, and misconfigurations happen all the time. No software, firmware, or hardware company is immune. More effort is needed as part of development and quality assurance, but even for the best organizations, it is possible for a series of mistakes to be made. That is why it is important to not only invest in defense and prevention but also architect ways to securely recover and resolve issues when they arise.

This event has a combination of attributes that amplify the impacts: the issue causes catastrophic system impacts (i.e. the dreaded BSOD), across a large number of systems, in Critical Infrastructure sectors, and the offending code possesses deep permissions within the computing stack.
This is the case we are seeing with Crowdstrike.
This outage reinforces the fact that cybersecurity solutions mitigate risks but also can become a source of risk. Mistakes were made. Trust was lost. The entire cybersecurity industry will be scrutinized, and that is probably the only good outcome of this mess.
Matthew Rosenquist is an industry-recognized pragmatic, passionate, and innovative strategic security expert with 28 years of experience. He thrives in challenging cybersecurity environments and in the face of ever shifting threats. A leader in identifying opportunities, driving industry change, and building mature security organizations, Matthew delivers capabilities for sustainable security postures. He has experience in protecting billions of dollars of corporate assets, consulting across industry verticals, understanding current and emerging risks, communicating opportunities, forging internal cooperation and executive buy-in, and developing practical strategies. Matthew is a trusted advisor, security expert, and evangelist for academia, businesses, and governments around the world. A public advocate for best-practices, and communicating the risks and opportunities emerging in cybersecurity. He delivers engaging keynotes, speeches, interviews, and consulting sessions at conferences and to audiences around the globe. He has attracted a large social following of security peers, is an active member on advisory boards, and quoted in news, magazines, and books. Matthew is a recognized industry expert, speaker, and leader who enjoys the pursuit of achieving optimal cybersecurity. Matthew Rosenquist is experienced in building world class teams and capabilities, managing security operations, evangelizing best-practices to the market, developing security products, and improving corporate security services.
Leave your comments
Post comment as a guest